1. Introduction: Redefining Data Security in the Cloud
Data security in the cloud era, as outlined by frameworks from IBM and NIST SP 800-144, is the collection of procedures and technologies designed to address external and internal threats as organizations increasingly outsource their data, applications, and infrastructure. This migration from controlled on-premise data centers to dynamic cloud services demands a fundamental re-architecture of security strategy.
Cloud computing operates on three primary models, each presenting distinct security considerations:
- Infrastructure as a Service (IaaS): Offers foundational computing resources—servers, hardware, networking, and storage—on demand. The customer organization manages the operating system, data, and applications, while the cloud provider manages the underlying physical infrastructure.
- Platform as a Service (PaaS): Provides a managed framework for application development, where the provider handles the underlying operating systems, software updates, and infrastructure, allowing developers to focus solely on their code.
- Software as a Service (SaaS): Delivers cloud-based software, typically on a subscription basis, with the third-party provider managing all technical aspects, including data, servers, and storage.
Each of these models abstracts different layers of the technology stack, but in doing so, they systematically dismantle the traditional security perimeter, forcing a strategic shift from protecting networks to protecting identities and data. Traditional on-premise security was built around a strong network perimeter—a digital castle wall to protect internal resources. In the cloud, this model is dangerously obsolete. Services are distributed and accessed from outside the corporate network, making identity and data the new, definitive perimeters.
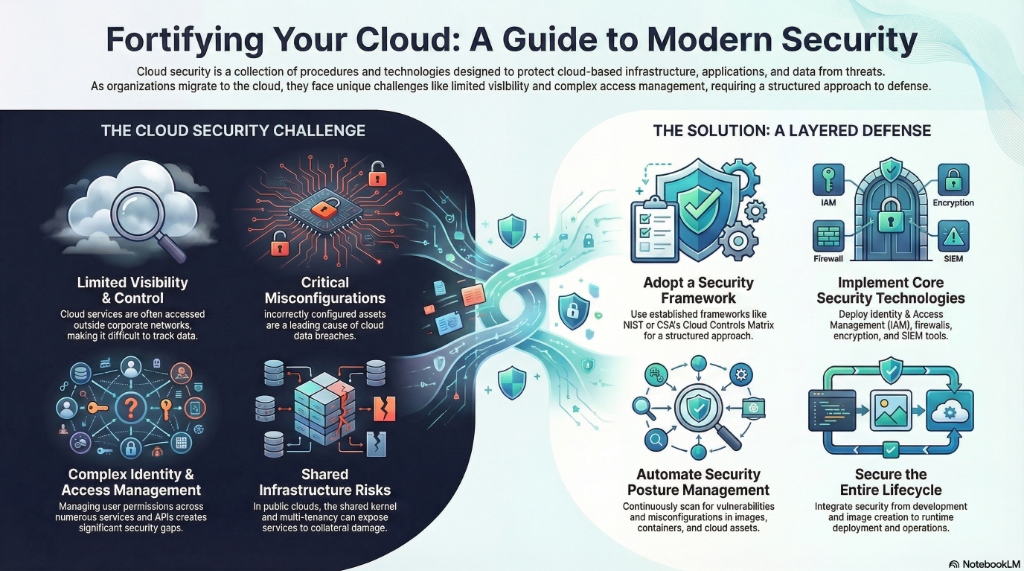
Fortifying Your Cloud: Challenges, Solutions, and Layered Defense Strategies
2. Foundational Principles: The New Rules of Engagement
2.1. The Shared Responsibility Model
A core concept in cloud security is the Shared Responsibility Model. Cloud Service Providers (CSPs) follow best practices to protect their global infrastructure, including the physical security of their data centers and the integrity of their servers. However, the responsibility for securing the data, applications, user access, and workloads that a customer runs on that cloud infrastructure remains squarely with the customer organization.
2.2. Zero Trust: The Modern Security Backbone
The Zero Trust security model has emerged as the modern backbone for cloud defense. This approach shifts security away from the outdated concept of a trusted internal network and an untrusted external one. Instead, Zero Trust operates on the principle that trust is never assumed and verification is required from every user and device attempting to access resources, regardless of their location.
This "never trust, always verify" principle is the essential strategic response to the modern threat landscape, where risks like misconfigurations, compromised credentials, and insider threats render perimeter-based trust models dangerously obsolete.
3. The Modern Cloud Threat Landscape
The shift to the cloud introduces unique security challenges and threats:
- Misconfigurations: A significant portion of data breaches are not the result of sophisticated attacks but of simple misconfigured assets, such as leaving default administrative passwords in place or failing to set correct privacy settings on cloud storage.
- Lack of Visibility and Shadow IT: When cloud services are accessed outside of corporate networks and through third-party applications, it becomes difficult to track how data is accessed and by whom, leading to "shadow IT."
- Credential & Secret Management: A critical risk in modern development is embedding clear text secrets—such as passwords, API keys, or private keys—directly into container images.
- Insecure APIs: Applications and interfaces are primary targets for attackers. Insecure APIs can expose application logic and sensitive data if not properly designed, authenticated, and monitored.
- Insider Risk: This threat arises from authorized users who either have excessive access privileges or intentionally abuse them.
- Untrusted Components: The ease of reusing third-party software components, such as container images from public registries, introduces the risk of deploying untrusted code containing malware or vulnerabilities.
4. Core Pillars of Cloud Data Protection
4.1. Data Lifecycle Protection
Protecting data itself is paramount. This requires a multi-layered approach:
- Encryption: Encryption is a non-negotiable control for rendering data unintelligible to unauthorized parties. Data must be encrypted both at rest (when stored in databases or object storage) and in transit (when moving between services or to end-users).
- Key Management: This involves the centralized management and control of the cryptographic keys used for encryption and decryption, emphasizing the need for secure generation, storage, and rotation of keys.
- Data Loss Prevention (DLP): This is a set of tools and processes designed to protect regulated cloud data using a combination of remediation alerts, encryption, and other preventive measures.
4.2. Identity and Access Security
With the dissolution of the network perimeter, identity has become the primary control plane for security.
Identity and Access Management (IAM) is a policy-driven framework for creating and managing digital identities. A robust IAM strategy includes:
- Identity Providers (IdP): Services that authenticate a user's identity.
- Single Sign-On (SSO): A system that allows a user to authenticate once and gain access to multiple applications.
- Multi-Factor Authentication (MFA): A critical security layer that strengthens authentication by requiring two or more verification methods.
- Access Control: Managing and restricting user access based on the principle of least privilege.
4.3. Network Security Modernization
Network security has evolved to protect virtualized and distributed cloud environments:
- Cloud Firewall / Web Application Firewall (WAF): A virtual security barrier hosted in the cloud to protect infrastructure from malicious traffic, blocking threats like DDoS attacks, malicious bot activity, and web application exploits.
- Micro-segmentation: Separating inter-container traffic into discrete virtual networks based on sensitivity, containing the "blast radius" of a breach.
5. Securing Modern Architectures
5.1. Secure DevOps (DevSecOps)
In a containerized model, security responsibility shifts "left," moving earlier in the development lifecycle. The DevSecOps model integrates security practices directly into the CI/CD pipeline.
The secure container lifecycle follows these key stages:
- Image Creation: Developers package applications, their dependencies, and configuration into container images.
- Testing and Accreditation: Before an image is stored, it must pass through an automated quality gate that scans for vulnerabilities and configuration defects.
- Registry Storage: Approved and cryptographically signed images are stored in a trusted, private registry.
- Deployment: An orchestrator (like Kubernetes) pulls trusted images from the approved registry and deploys them as running containers.
This model embraces the principle of immutability. Running containers are never patched or modified. Instead, to update or fix a vulnerability, a new image is built, scanned, and deployed to replace the old one, fundamentally eliminating configuration drift.
5.2. Container and Kubernetes Security
A container ecosystem consists of multiple layers, each with unique risks and countermeasures:
- Images
- Risk: Vulnerabilities in software libraries, insecure configuration defects, embedded malware, and clear text secrets.
- Countermeasure: Use container-specific vulnerability management tools. Enforce secure configuration best practices. Store secrets in an external vault, never in the image.
- Registries
- Risk: Insecure, unencrypted connections and insufficient authentication.
- Countermeasure: Enforce encrypted (TLS) connections. Require strong authentication and implement role-based access control (RBAC).
- Orchestrators (e.g., Kubernetes)
- Risk: Unbounded administrative access and mixing workloads of different sensitivity levels.
- Countermeasure: Implement a least-privilege access model. Configure the orchestrator to isolate deployments based on data sensitivity.
- Container Runtimes
- Risk: Vulnerabilities within the runtime software itself or insecure configurations.
- Countermeasure: Continuously monitor for vulnerabilities and apply patches. Use Mandatory Access Control (MAC) technologies like SELinux or AppArmor.
6. Advanced Security Tooling and Operations
A mature cloud security program leverages specialized tooling designed for dynamic, large-scale environments:
- Cloud Security Posture Management (CSPM): These solutions continuously monitor cloud environments to discover insecure settings, organize core security components like IAM, and help manage regulatory compliance.
- Security Information and Event Management (SIEM): A security orchestration solution that automates threat monitoring, detection, and response by aggregating and correlating log data.
- Cloud Workload Protection Platform (CWPP): A security solution specifically designed to protect workloads (VMs, containers, serverless functions) across any cloud environment.
- Cloud Infrastructure Entitlement Management (CIEM): Tools that specialize in managing permissions and entitlements in complex cloud environments, helping enforce least privilege.
7. Governance, Risk, and Compliance (GRC) in the Cloud
The Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM) has become a de-facto standard for cloud security assurance and compliance. It is a comprehensive cybersecurity control framework with 197 control objectives across 17 domains, covering all key aspects of cloud technology.
Key domains covered by the CCM include:
- GRC: Governance, Risk Management, & Compliance
- IAM: Identity & Access Management
- DSP: Data Security & Privacy
- A&A: Audit & Assurance
8. Approaches of Major Cloud Providers
- Amazon Web Services (AWS): Emphasizes that security is its top priority with a secure-by-design global infrastructure. AWS focuses heavily on security automation to enable teams to move fast while staying secure.
- Google Cloud: Focuses on leveraging AI-driven protection with Gemini, vast global threat intelligence from Mandiant and VirusTotal, and a secure-by-design foundation.
- Oracle Cloud Infrastructure (OCI): Promotes a security model that is foundational, built-in, simple, and prescriptive. Key services include Cloud Guard, Security Zones, and Data Safe.
- Microsoft Azure: Promotes the Microsoft cloud security benchmark (MCSB) as a comprehensive framework for securing cloud solutions with prescriptive security baselines.
9. Lessons Learned: Common Cloud Security Failure Patterns
Analyzing common failure patterns provides invaluable lessons for building a more resilient security strategy:
Scenario 1: The Silent Breach from the 'Temporary' Storage Bucket
It begins with a developer, rushing to meet a deadline, who provisions a new cloud storage bucket and sets its permissions to "public" for a quick data transfer, intending to fix it later. "Later" never comes. Weeks pass until a frantic, late-night call from the compliance officer: a security researcher has found terabytes of sensitive customer data indexed by public search engines. This isn't a sophisticated hack; it's a simple, preventable error that leads to emergency board meetings, regulatory fines, and irreparable reputational damage. It is a harsh lesson in the absolute necessity of automated posture management.
Scenario 2: The Cascading Failure from a Single Compromised Credential
An attacker sends a clever phishing email to a developer, who clicks a link and inadvertently gives up their login credentials. Because the developer's IAM account was configured with overly broad permissions, the attacker doesn't just gain access to a single server. They find embedded API keys in a code repository, pivot to production systems, and begin a slow, methodical exfiltration of the company's most valuable intellectual property. The breach isn't discovered for months. This illustrates why a strict, Zero Trust model with least-privilege access and mandatory MFA is not a suggestion—it's a requirement for survival.
Scenario 3: The Ticking Time Bomb in the Public Registry
To accelerate development, a team pulls a popular open-source container image from a public registry. The image works perfectly, but it contains a critical, known vulnerability that was disclosed weeks ago. Lacking an integrated DevSecOps pipeline to scan images before deployment, the ticking time bomb is deployed directly into production. An automated scanner, operated by an attacker, finds the vulnerable service within hours and exploits it to gain a foothold inside the network. This highlights the non-negotiable mandate for embedding security scanning directly into the CI/CD pipeline.
10. An Enterprise Roadmap to Mature Cloud Security
A strategic roadmap aligns with the five pillars of the NIST Cybersecurity Framework: Identify, Protect, Detect, Respond, and Recover.
Identify:
- Mandate a formal review of the Shared Responsibility Model for every cloud service.
- Deploy automated asset discovery tools to eliminate 100% of shadow IT within six months.
Protect:
- Enforce a comprehensive IAM strategy grounded in Zero Trust, with MFA as a mandatory baseline.
- Integrate automated vulnerability and compliance scanning directly into the CI/CD pipeline.
- Implement universal encryption for all data, both in transit and at rest.
Detect:
- Deploy a CSPM tool to continuously monitor for misconfigurations and compliance drift.
- Utilize a SIEM solution to aggregate logs and telemetry for unified threat detection.
Respond:
- Develop and drill an incident response plan specifically architected for cloud environments.
- Leverage security automation to rapidly isolate compromised resources.
Recover:
- Maintain and regularly test robust backup and disaster recovery plans.
- Ensure data retention and disposal policies are programmatically enforced.
11. Conclusion: Moving Forward with Confidence
Securing the enterprise in the cloud era is not a one-time project but an ongoing strategic process. It demands a cultural shift toward shared responsibility, the adoption of modern tools built for automation and scale, and a strong architectural foundation built on principles like Zero Trust.
By embedding security throughout the entire application and data lifecycle—from the first line of code to production monitoring—organizations can confidently embrace the cloud, accelerating innovation without compromising their security posture.